
IPFS & libp2p Devs Go Independent: Meet Interplanetary Shipyard
Meet the team behind Interplanetary Shipyard, the newly created entity of many core maintainers behind the most popular implementations of IPFS and libp2p.

The public-good IPFS gateways at ipfs.io and dweb.link have played a foundational role in IPFS adoption—serving over 614 million requests and 45TB of data to 10 million users daily. However, this centralized infrastructure has become a major obstacle to sustainability and decentralization.
Our traffic analysis identifies three main user categories:
We propose a targeted transition plan to help each group move toward decentralized, verifiable content retrieval. This shift is made possible by recent Shipyard innovations:
Our analysis shows:
@helia/verified-fetchinbrowser.link for secure, offline-ready accessThis strategy aligns with IPFS’s core vision of resiliency and verifiability through decentralization and offers practical solutions for sustainable content delivery at scale.
IPFS public gateways were instrumental in driving early adoption by bridging Web2 and Web3. However, their centralized architecture now presents serious challenges to scalability, security, and protocol evolution.
This article outlines a strategic transition plan grounded in real gateway traffic data. We identify how different user types interact with IPFS content and describe drop-in tools to shift from centralized gateways to decentralized, verifiable alternatives.
The IPFS gateways at ipfs.io and dweb.link allow standard web clients to retrieve IPFS content via HTTP without verifying content-addressed data on their own
. While this accessibility has driven adoption, it has also created technical and economic burdens:
To make IPFS sustainable and scalable, we must move beyond public-good gateways.
From May 12–14, 2025, we analysed gateway traffic, filtering out known abuse via Cloudflare and Badbits. Although imperfect, this data gives a representative view of usage patterns across three user categories:
Direct visitors loading IPFS-hosted static sites or dApps via ipfs.io or dweb.link. These appear as modern browser user agents without cross-origin headers.
Cross-origin media, JSON, or resource fetches embedded in websites or mobile/desktop apps. These use IPFS gateways as a CDN for partial content rather than full pages.
Backend scripts, crawlers, proxy services, and other headless HTTP clients. These should ideally run their own IPFS nodes or gateways.
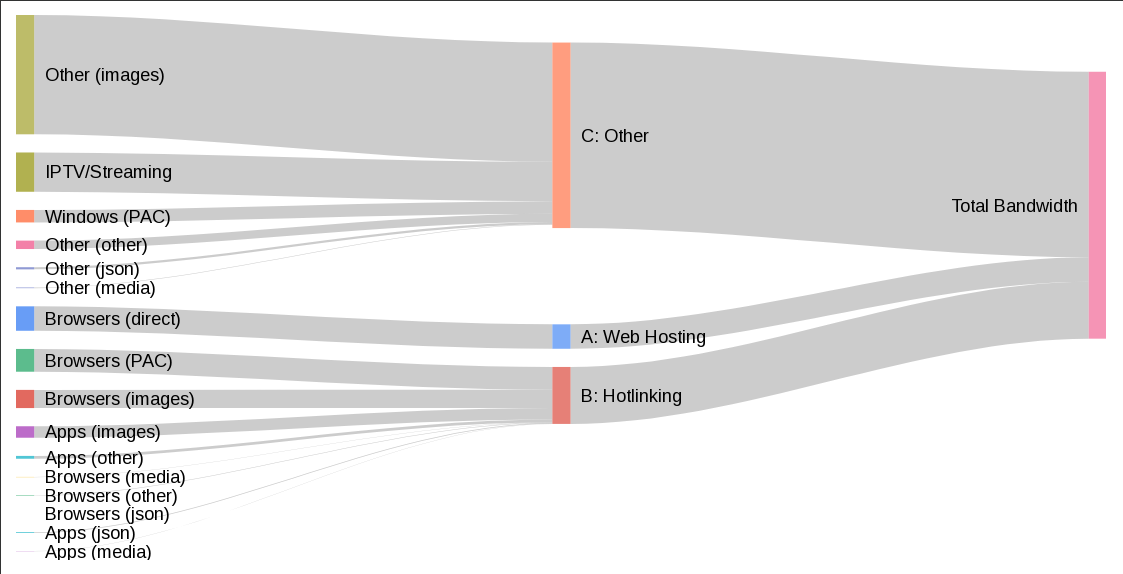
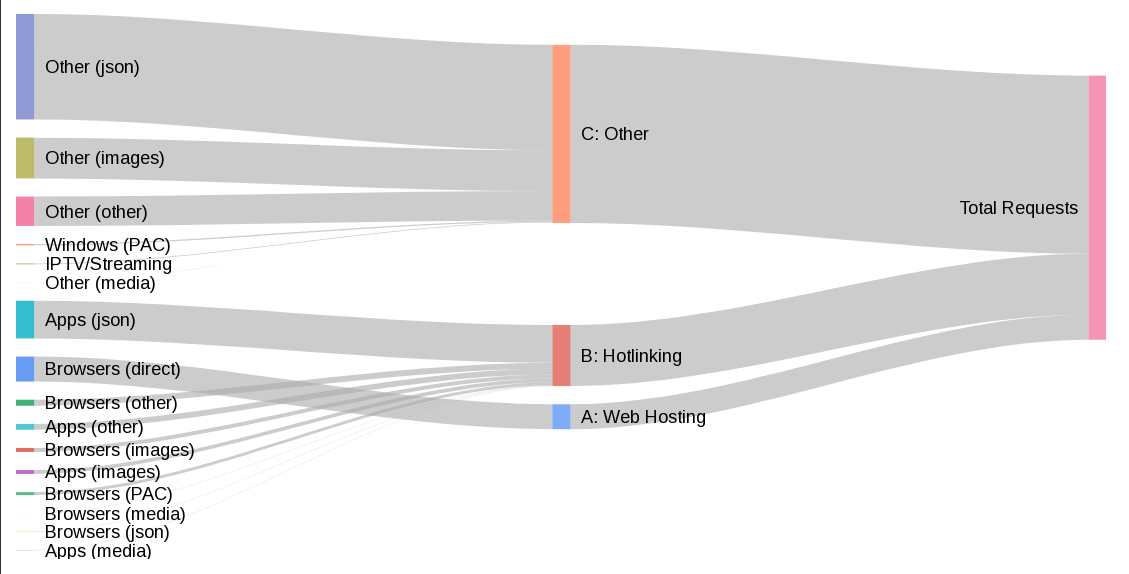
The takeaway: the vast majority of traffic comes from clients that could—and should—be using native tooling to fetch directly from the network. Only about one-third is web browser–based. Still, it was important to develop tools to support browser users, so we had a clear migration path for that segment before moving into the next phase of the transition roadmap. Without a viable upgrade strategy for browser users, it would be difficult to justify limiting automated clients that can easily masquerade as browsers. By establishing a migration path for real browser users, we’ve effectively closed off this loophole as a way to disguise bogus traffic going forward.
Go-http-client (33.3% bandwidth / 27.2% requests)go-resty, node-fetch, Lavf, etc.Most IPFS gateway usage today stems from backend services treating ipfs.io as a free CDN—undermining decentralization and harming performance for legitimate browser users. And some of the largest share of user agents we see are from some of our best supported languages, Go and NodeJS, and as such should be easy candidates for migration to native retrieval.
We propose a phased transition, offering targeted tools for each user type:
inbrowser.linkRedirect organic users to the Service Worker Gateway
at https://inbrowser.link. This maintains the same user experience while enabling local verification, offline access, and better security.
@helia/verified-fetchEncourage apps that hotlink images or JSON to switch to Drop-In Service Worker
. Or for those looking for more verification and resiliency, there’s Verified Fetch
which offers trustless content retrieval and automatic fallback to multiple providers—drop-in compatible with fetch().
For backend and automated clients, we recommend running dedicated IPFS nodes or gateways using tools like Rainbow and Someguy . These services shouldn’t rely on the public-good gateway at all.
fetch() Web APIipfs://, ipns://, and https://inbrowser.link)dweb.link subdomain gatewaydelegated-ipfs.dev (or self-hosted)Tools like Verified Fetch, Service Worker Gateway, and delegated routing are live and ready.
We’re sharing migration guides, offering support, and reaching out to top gateway users across all categories.
inbrowser.linkipfs.io and dweb.linkThis transition is about more than infrastructure—it’s about returning IPFS to its decentralized roots.
By decentralizing retrieval, we improve:
We’re building a more robust IPFS, one that scales with its users instead of against them.
We’re actively monitoring issues and providing support across our tool chain:
You can also find migration guides and community support at discuss.ipfs.tech .
If you’re confused about how to approach this migration, or how this will affect you, please get in touch with us. Either via the IPFS discussion forums, GitHub, Slack, or other mediums, as outlined on https://ipfs.tech/community/ .

Meet the team behind Interplanetary Shipyard, the newly created entity of many core maintainers behind the most popular implementations of IPFS and libp2p.
The Bybit hack revealed several security failures, this post examines whether IPFS could have helped prevent the hack and practical solutions for dapp developers.
Our free IPFS tools and integrations have over 75 million monthly active users around the globe.
Help Fund Shipyard